- In this demo, we are using a remote machine (Kali Linux) to SSH into another remote machine (Metasploitable Linux).
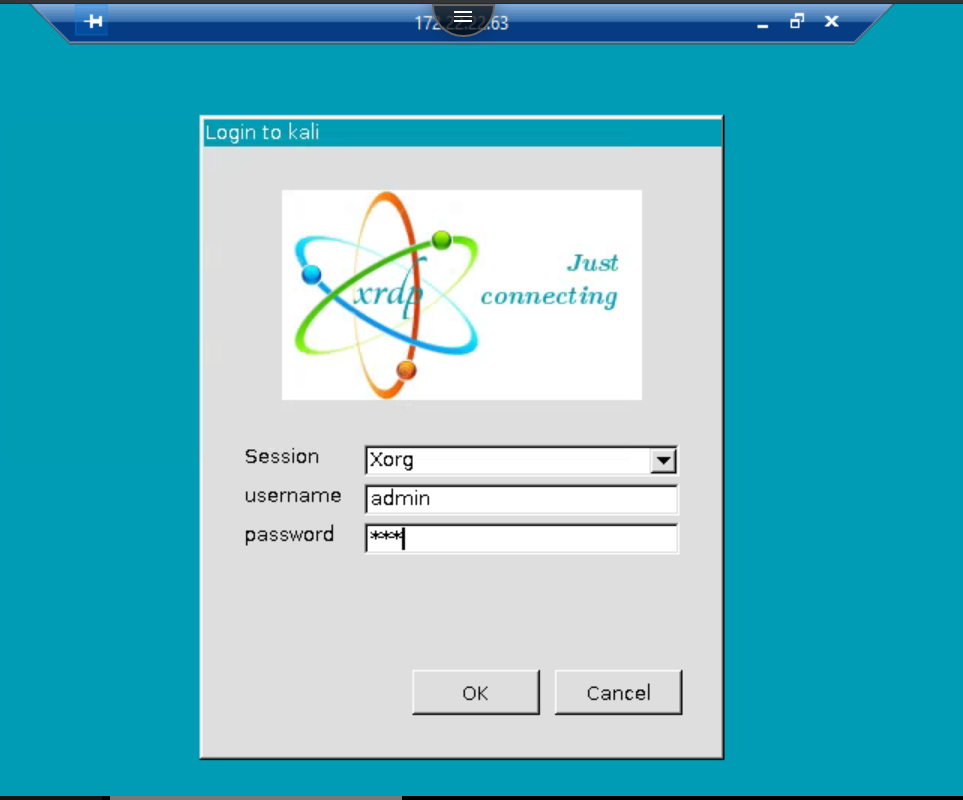
- Create and connect to your machine. In this example, we’re connecting and using Kali Linux. Provide the user credentials listed in the box to access.
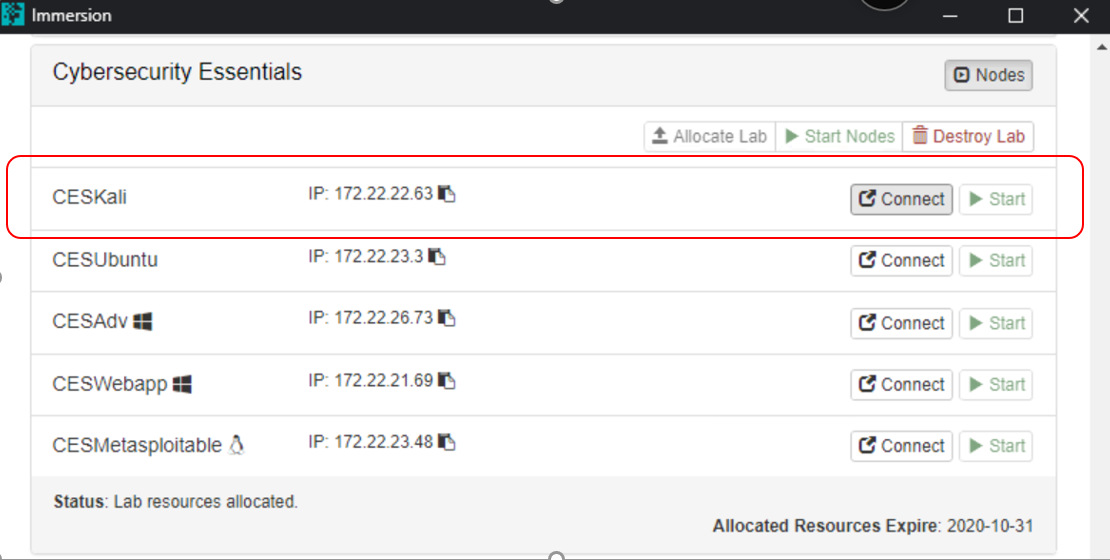
- Click ‘Connect’.
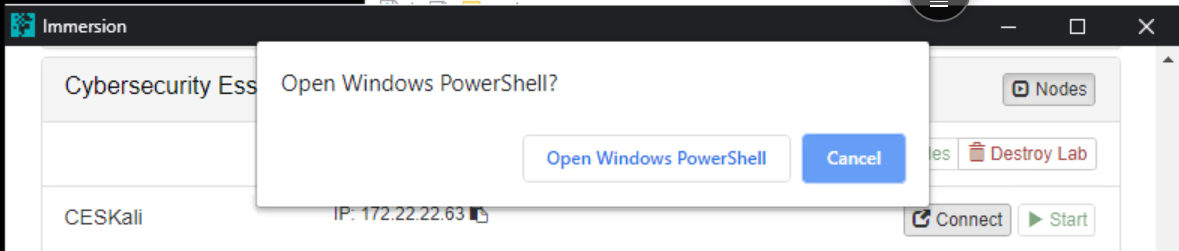
- Click on "Open Windows PowerShell"
- Click ‘Connect’.
- Click ‘Yes’.
- Login to Kali, using the credentials provided in the first image above.
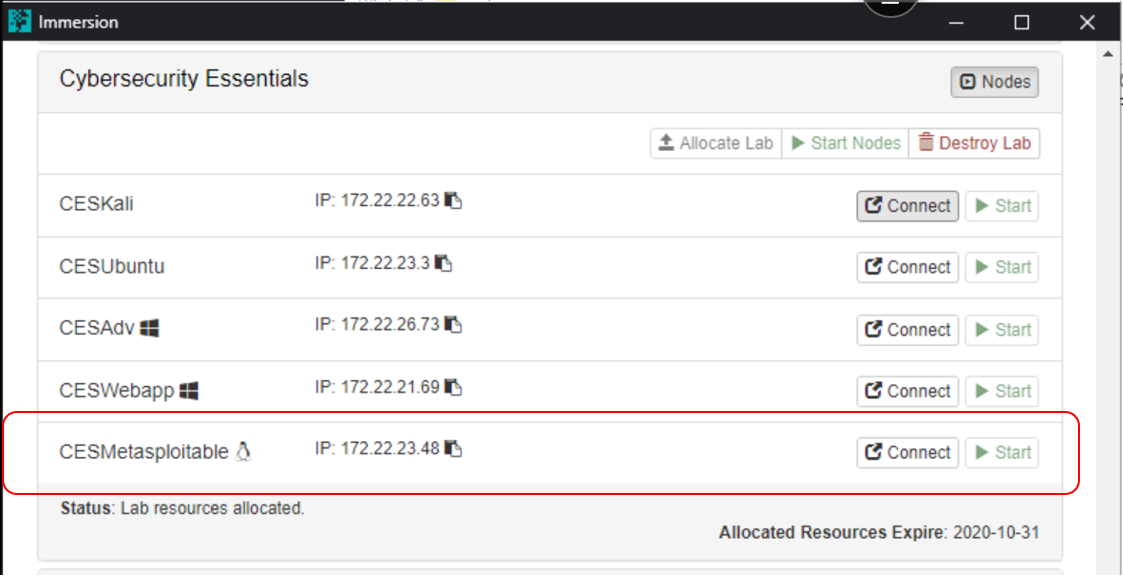
- Go to the Cyber Hub Proving grounds, and find the Metasploitable Linux Machine. Click the blue button ‘Create’.
- Make sure you have the desired machine Created and ‘READY’. Do not connect, you’ll be doing so through SSH from the Terminal in Kali Linux, using the credentials listed below.
- Once in the Kali Linux environment, open the Terminal.
- You are currently logged in as username student; in order to access the Metasploitable Linux, the username will need to change from ‘student’ to ‘vagrant’, which is the username for the Metasploitable Linux.
- Below is the desired machine’s IP, Username, and Password
Username : vagrant
Password : vagrant
- SSH from your machine to the other.
ssh <ip of machine you want to connect to> -l <username>
- You will then be prompt to provide the password of the desired machine.
<username>@<ip of machine you want to connect to>: